The cyber security landscape has changed drastically in the last decade. We hear it all the time with the databases of large, trusted companies being hacked: Yahoo with 3 billion user accounts, Marriott International with 500 million customer accounts, credit reporting agency Equifax with 143 million consumers and TJX Companies with 94 million credit cards exposed.
These are only the data breaches that we see in the headlines. What about all the small- to medium-sized companies that never make the headlines? Could your company be next?
Consider this scenario: It is a normal day at work and you see strange file extensions as you scan through your emails. You open one of these files and a strange message appears on your screen demanding payment with a timer counting down to your companies’ network demise. How did this happen? A malicious phishing email and it only took one employee, one email and one ill-fated click.
What is Phishing?
A phishing scam, or phishing attack, occurs when a cyber criminal sends an email posing as someone else to entice or lure you to provide sensitive personal or company information. They try to extract sensitive information such as usernames and passwords, credit card information, personal identifiers and account information. They attempt to elicit fear, a sense of urgency, or curiosity causing you to open an attachment or click on a link which may install malware, spyware or a virus on your computer.
“Phishing attempts have grown 65 percent in the last year,” according to PhishMe’s Enterprise Phishing Resiliency and Defense Report. Verizon reports that “93 percent of cyberattacks originate via phishing, with a total yearly cost to U.S. businesses of $500 million.”
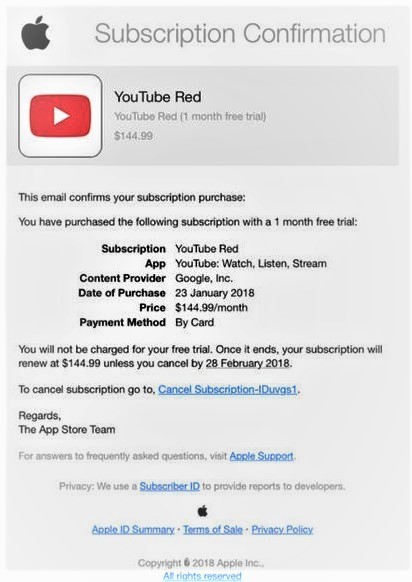
Here is an example of a recent phishing attempt published on Apple’s website:
While this looks legitimate, the point of the scam is to have the user click on the link to cancel the subscription. Once they click, they will be asked for a range of sensitive information. While most of us would catch on to the scam at some point, some do not. Admittedly, it is a convincing email.
More recently, there is an increasing amount of targeted attacks referred to as “spear phishing.” This occurs when a criminal uses a more personalized approach to lure its victim. These attacks can be highly effective because the perpetrator uses language tailored to the targeted individual. The email may appear to be coming from a client, your boss, an internal department or a vendor. Imagine, for example, if your boss invites you to attend a webinar and asks you to confirm your attendance by logging into your outlook account. Using a malicious link in the email, the spear phishing allows criminals to go after your sensitive information and, if credentials are gained, the possibility of causing significant damage to your business.
Three ways to keep your business safe
There are a number of steps that employers can take to lower the number of problems with security breaches. Increase employee training and make it a part of your company culture. Continuous security awareness training, on average, provides 37 times the return on a company’s investment.
Invest in a security awareness and a phishing defense tool. There are several companies that offer tools (free and paid) to filter and provide a defense in phishing email attacks against your organization: Phishme, KnowBe4, Webroot, Barracuda, and Duo are just a few. Do the research and find a tool that best fits your company’s needs and reduce your likelihood of a successful attack.
Make sure you have successfully implemented the following authentication methods in your domain. These are standards that will help validate your email and are designed to protect your email from potential spammers and phishers. Research and implement these:
- SPF (Sender Policy Framework) validates that your email address is coming from your mail server by authorizing your sending email address to your company’s internet domains IP (internet protocol) address.
- DKIM (Domain Keys Identified Mail) proves that the contents of an email have not been tampered with, that the headers in the email have not changed since the original sender sent the email, and that the sender of the email owns the domain or is authorized to send the email by the owner of the domain.
- DMARC (Domain-Based Message Authentication) is an added authentication method that requires both SPF and DKIM to pass, determining that at least one of them is aligned. This prevents accepting malicious emails that are pretending to be someone else. Google recommends this method for bulk email senders, plus Gmail and Microsoft are quickly adopting DMARC into their filtering methods.
It’s time to get in front of these threats. Become knowledgeable on how to install the proper tools and educate your employees in security awareness to protect your business. Contact us at BCN services to find out how we can help or for more information on this topic.